Single sign on, sooner or later become a part of user management services. Office 365 gives you several ways to implement single sign on identity through several way such as:
- Cloud identity: Office 365 as login provider. We simply said out of box experience on Microsoft Platform to authenticate the identity across Microsoft product such as OneDrive, Skype, and Yammer.
- Synchronized Identity: Office 365 as a login provider and then synchronized with on-premises directory such as LDAP and ADFS. The user uses same password between office 365 and On-premise.
- Federated identity: Third party authentication is used such as JASIG CAS or ADFS Login page, Office 365 works as redirection provider only, the authentication and authorization is done by 3rd party authentication provider.
You can read the detail about the post https://blogs.office.com/2014/05/13/choosing-a-sign-in-model-for-office-365/. This post will make an effort to explore several scenario that can be done for federated identity
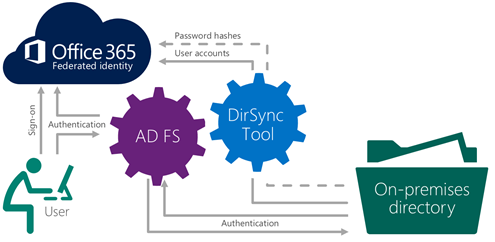
Federated Identity with ADFS
This approach is the most recommended model to integrate your on-premise infrastructure and Office 365. The authentication will support both Office 365 web client and desktop client. Give you the most fruitful experience on SSO Federated identity scenario. Please find this documentation if you want to implement Office 365 and ADFS 2.o (at this time of the writing Microsoft still doesn't have official guide for ADS 3.0 , please find this post to setup with ADFS 3.0 .
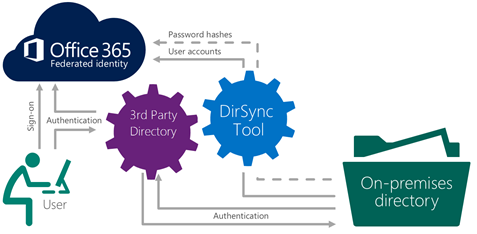
Federated Identity with 3rd Party Provider (SAML 2.0)
This approach is chosen when you already has existing infrastructure such as Shibboleth (identity provider) or others. The authentication currently only support web client and no support for desktop client. Please find this documentation if you want to implement Office 365 with Shibboleth. For others provider, please find on this link. If you feel that your identity provider is not mentioned, please find this document to understand the specification that needed to support.
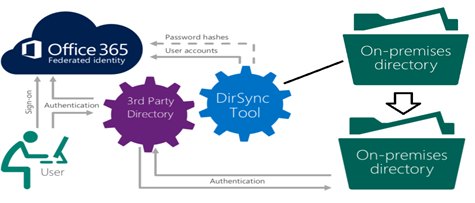
Federated Identity with Two or More Directory
This happen when you already have 3rd party provider but need client authentication, so the idea is you authenticate with the first directory such as LDAP and create a new directory ADFS that sync with the cloud for authentication inside the organization or client authentication. The two directory itself will sync through custom services application. This is still experimental and will discuss it further on the next post.